Permanently disabling interdependent services and service dependencies
Many CIS Benchmarks control checks if a specific service is ‘disabled’ and/or ‘not running’. One key example is the control ‘Ensure CUPS is not enabled’ from the ‘CIS Debian Linux 10 Benchmark’.
Following the remediation procedure you may attempt to disable the service using the following command:
systemctl --now disable cups.serviceThis command should instantly stop the cups service, and also prevent it from restarting at boot-time. However, cups is a downstream dependency of the service cups-browsed, which is not disabled. Consequently, cups can restart after a reboot. To find such dependencies you can use the following command:
systemctl --reverse list-dependencies cups.serviceTo ensure that disabled services don’t restart unexpectedly, you can mask a service in addition to disabling it, using the following command:
systemctl mask cups.serviceMasking a service renders it invisible to other services, effectively solving the issue.
Find and fix the security risks that pose the biggest threat to your business.
Why you should use apt purge instead of apt remove
Almost all CIS Benchmarks require the removal of one software package or another. For Debian based distributions, the APT package manager is used, and in older CIS Benchmarks (Debian 8/9, Ubuntu 14.04, or the CIS Distribution Independent Linux Benchmark) the remediation procedure suggests removing a package using the following command:
apt remove <package>Or
apt-get remove <package>However, newer CIS benchmarks have replaced apt-get remove with apt purge.
apt purge <package>A common misconception is that apt-get remove deletes all potentially harmful files while only preserving the configuration of the software package for potential future use. Sometimes not the binary files themselves contain vulnerabilities, but also the additional files installed with the software package. For example, the NTP Vulnerability CVE-2016-0727, is a vulnerability in the cronjob accompanying the package. APT software packages allow the package maintainer to specify what files are to delete or to keep in case the package is removed by apt remove. Hence, the only way to be sure that all vulnerable pieces of an APT software package have been deleted from a system, is by using the apt purge command.
If you remove a package using apt remove, it will still show as installed in cnspec queries:
This is because under the hood, cnspec will check the packages state in /var/lib/dpkg/status or /var/lib/dpkg/status.d.
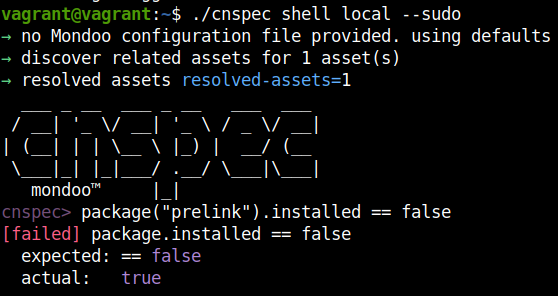
1. Let’s use cnspec to check if the package prelink is installed on our Ubuntu 22.04 test system, using cnspec shell local --sudo.
cnspec> package("prelink").installed == false[failed] package.installed == false expected: == false actual: true2. Now we remove the package using apt remove
.
vagrant@vagrant:~$ sudo apt remove prelink3. Doing the same query as above to check the installation status reveals, it’s still considered installed:
cnspec> package("prelink").installed == false
[failed] package.installed == false
expected: == false
actual: trueThe package state in /var/lib/dpkg/status is as follows:
Package: prelinkStatus: deinstall ok config-filesPriority: optional4. Now we use apt purge to remove the prelink package completely:
vagrant@vagrant:~$ sudo apt purge prelinkNow the package prelink has been removed from /var/lib/dpkg/status.
5. The cnspec query below confirms the successful deinstallation:
cnspec> package("prelink").installed == false
[ok] value: falseIn conclusion, always use apt purge to remove packages to ensure proper hardening of your Debian-based systems.







