What is sudo CVE-2025-32463?
CVE‑2025‑32463 is a critical local privilege escalation vulnerability, in the widely used sudo utility for Unix-like operating systems, including Linux and macOS. sudo stands for "superuser do" or "substitute user do," because it enables users to temporarily run specific commands with elevated permissions without needing to log in directly as the superuser (root).
This CVE could allow a local attacker to trick sudo into loading and executing a malicious shared library using the user-specified root directory via the -R (--chroot) option. This means that an attacker with local access could prepare a writable directory with a fake /etc/nsswitch.conf and a malicious libnss_*.so library, and then load that code as root. Yikes!
Who is affected by CVE-2025-32463?
The vulnerability affects sudo versions 1.9.14 through 1.9.17, and is patched in version 1.9.17p1. Note that legacy versions of sudo (1.8.32 and earlier) are not vulnerable. In addition, this vulnerability can only be exploited if the sudoers configuration contains a per-command chroot directive matching the current host. Every major Linux distribution has issued security advisories, including Red Hat, SUSE, Debian, and Ubuntu. MacOS Sequoia, the current version, ships with sudo 1.9.13p2, and is also not vulnerable.
How exploitable is CVE-2025-32463?
The CVSS 3.1 scoring system measures the severity of a vulnerability, where severity reflects the potential consequences to confidentiality, integrity, and availability if the vulnerability were exploited. While this vulnerability is severe because it enables unchecked privilege escalation, it also requires an attacker to first have access to a valid account on a system. In addition, the system must be configured with an exploitable sudoers configuration. This means that it’s actually quite difficult for attackers to take advantage of, unless they’ve already gained access to the system AND the system is configured in an exploitable way. That’s where EPSS comes in.
CVSS (Severity) versus EPSS (Risk)
Where CVSS measures severity, the Exploit Prediction Scoring System (EPSS) measures risk. EPSS scores, recalculated daily, are the estimated probability that a vulnerability will be exploited within the next 30 days, with higher scores indicating a greater likelihood of exploitation. EPSS ratings comprise two parts: a probability and a percentile. An EPSS score of 56.74% (97th), for example, means that the vulnerability has a 56.74% likelihood of being exploited sometime in the coming month, and is more likely to be exploited than 97% of all other EPSS-scored vulnerabilities.
So what’s the EPSS rating for CVE-2025-32463? The EPSS score for this vulnerability is 0.27% (50th) (as of July 16th). This means that there’s only about a quarter of a percent likelihood of exploitation within 30 days. The EPSS percentile (relative to other CVEs) is set at 50th, which means that the vulnerability is more likely to be exploited than 50% of all other scored vulnerabilities, and ranks at the median.
The combination of high severity, low probability, and median percentile helps paint a more complete picture of the actual hazard posed by the vulnerability. Mondoo visualizes this relationship between vulnerability severity and risk in an area graph, to give security engineers an at-a-glance understanding of the threat posed by each CVE.
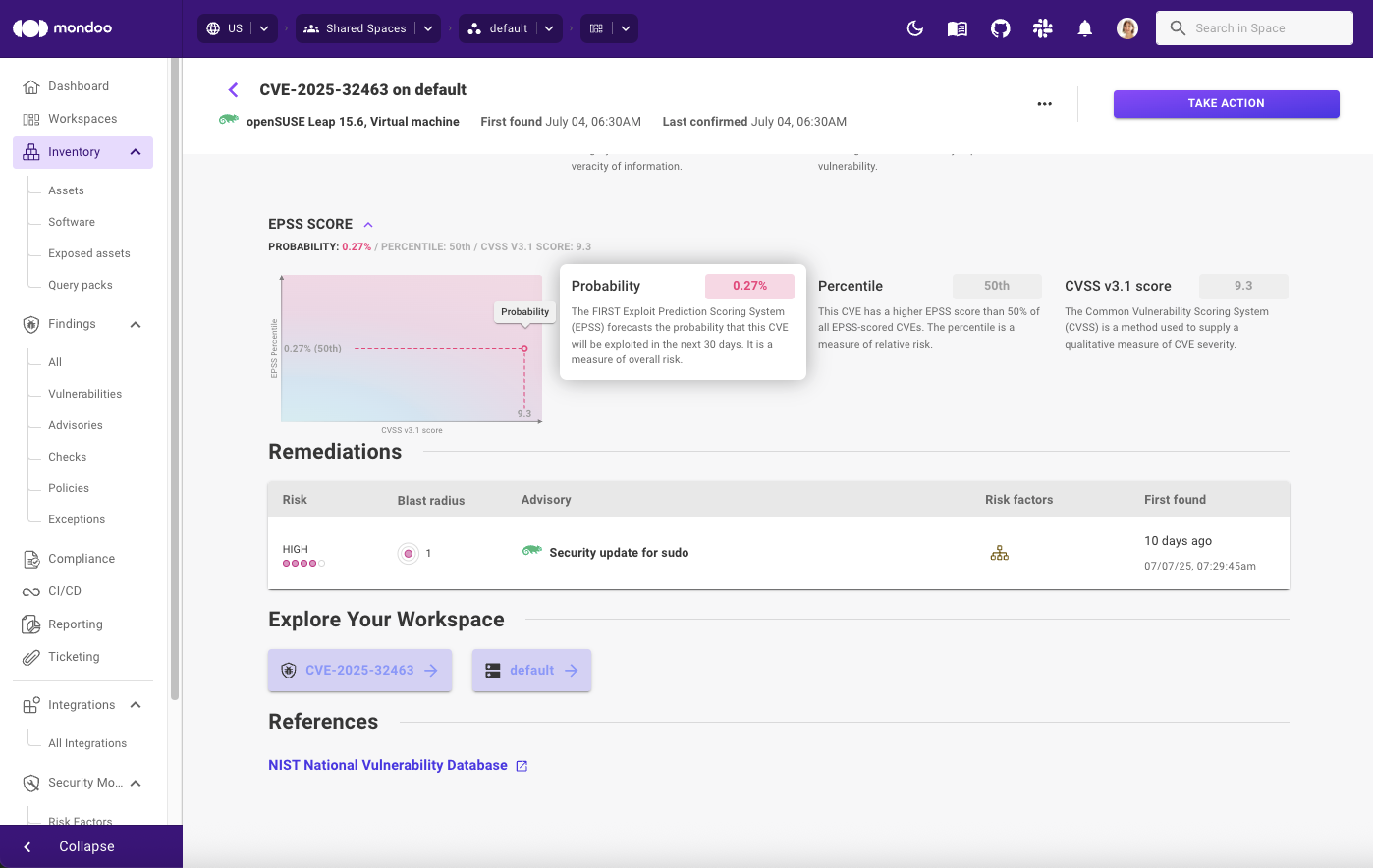
Vulnerability management tools should take the full spectrum of severity and risk into account to convey the true threat to the business. If a vulnerability is severe but extremely unlikely to be exploited, the risk attributed to the vulnerability should be lowered. Security teams are often tracking hundreds of vulnerabilities, many of which may require more immediate attention, such as the recent Chromium zero-day, to name but one.
Considering only the CVSS score, CVE-2025-32463 would be classified as a high or critical priority. But given the low chance of exploitation, Mondoo automatically adjusts the relative importance of this vulnerability. But that still isn’t the whole picture.
Contextual risk factors
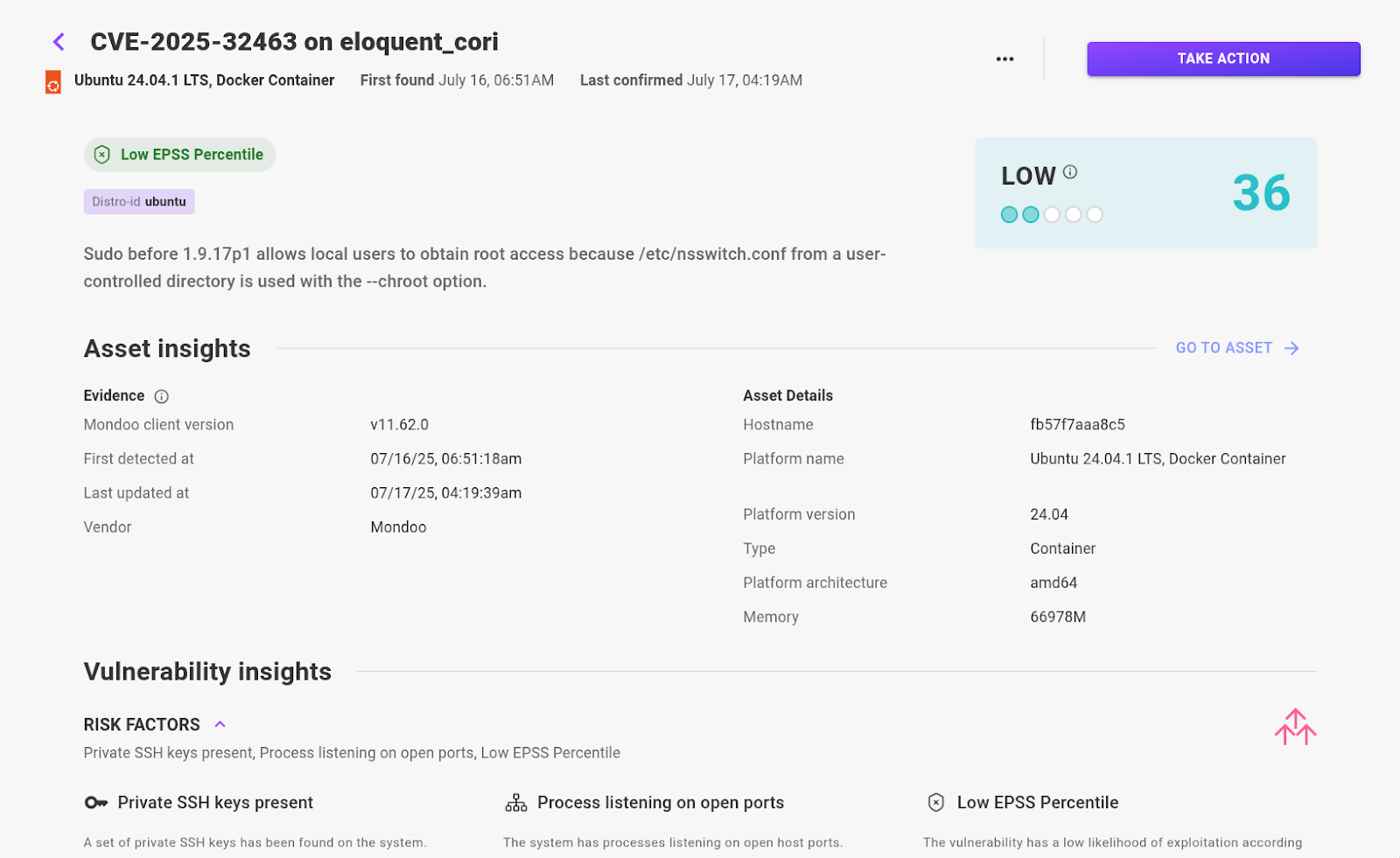
CVSS and EPSS scores are linked to the CVE itself, but they don’t offer any insight into the actual exposure that exists in your individual environment. This can only be determined when you have a full understanding of the context. For instance, in the case of CVE-2025-32463, are there any factors present that could increase or reduce the likelihood or impact of exploitation?
Factors that increase risk:
- The asset has a public IP on the internet
- The sshd process is active
- The sshd process is listening on an open port
- The asset has access to critical data
- Another vulnerability on the asset allows for remote code execution
Factors that reduce risk:
- A local firewall controls inbound network access
- The asset does not have access to critical data
- Restricted user access to the system
Mondoo scans for all these factors, displays them in the UI, and automatically adjusts priority scoring according to the actual risk in your environment. This means that you are focusing on the most critical issues and saving your security team hours of manual investigation.
How Mondoo helps remediate CVE-2025-32463
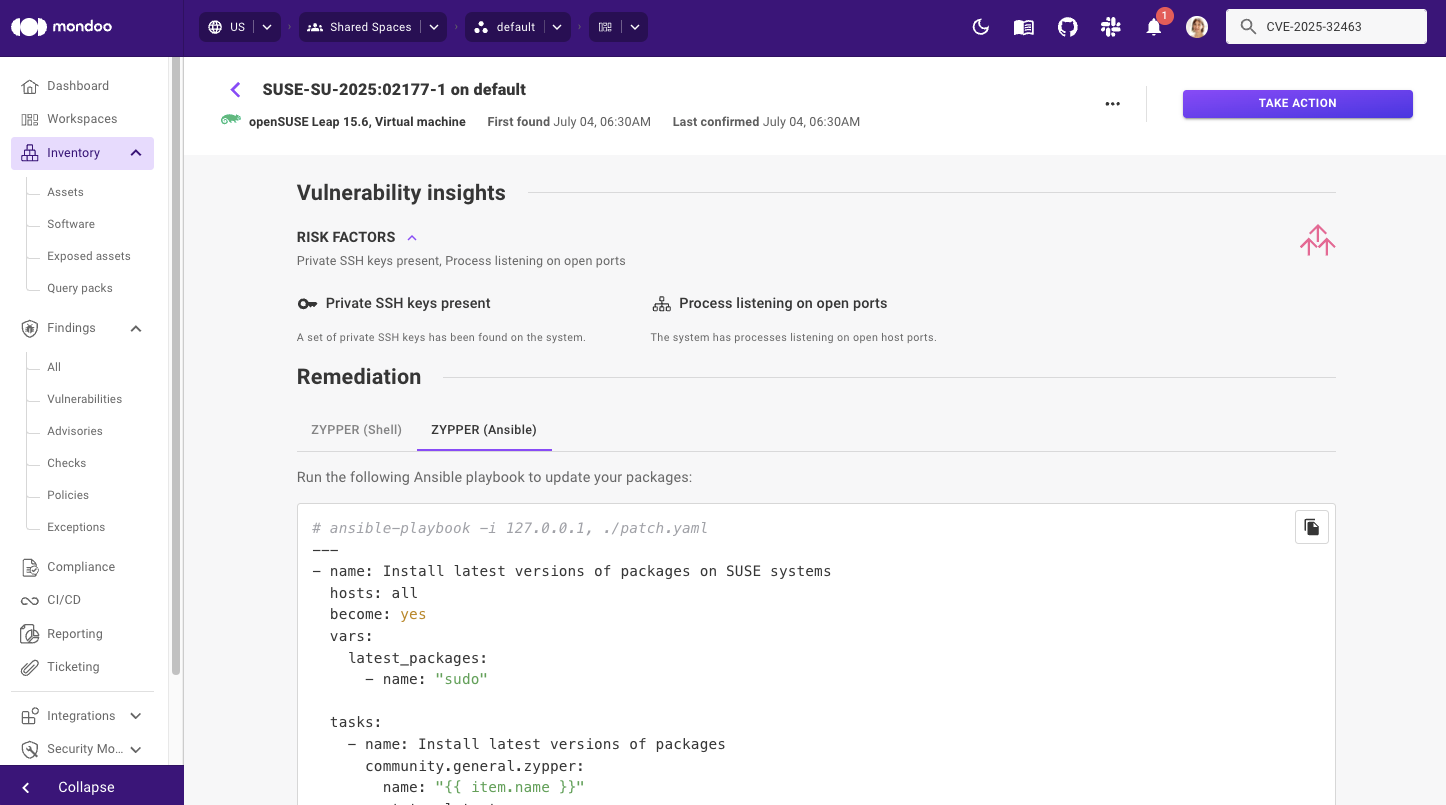
To remediate the vulnerability, you must update sudo to version 1.9.17p1 or later. To help you upgrade quickly and easily, Mondoo provides Ansible and Shell code snippets that can be deployed to roll out patches en masse.
Find and fix the security risks that pose the biggest threat to your business.
Remediate 3x faster with Mondoo Unified Exposure Management
Conclusion
As the saying goes, “If we treat everything as important, nothing is important.” The sudo vulnerability is an interesting example of why severity does not always equal risk. Several factors need to be considered to determine which vulnerabilities are truly critical in your environment and must be remediated first. Because manual investigations are very costly, teams need to rely on their vulnerability management tool to accurately assess risk based on contextual factors.
“Before Mondoo we had a sea of red with no clear path forward. By adopting Mondoo, we were able to identify the most important things to address so that by the time we had it fully enabled, we had only a handful of issues.”
Todd Bradfute, Senior Director of Security & Technology at SimpleRose
About Mondoo
Mondoo is a comprehensive exposure management platform that identifies, prioritizes, and addresses vulnerabilities and misconfigurations in your entire IT infrastructure from a single interface, covering on-prem, cloud, SaaS, endpoints, and the SDLC. Unlike siloed approaches that require you to continually switch consoles, Mondoo unifies findings in a single platform, surfacing the most critical risks across your entire environment so you can effectively optimize security efforts.
To learn more, schedule a demo with one of our experts.








